Value propositions IT controls and security
CIO, IT controller, CISO, and CFO, CEO
Your questions & needs
- You are facing security and compliance issues in your ERP / SAP systems.
- Your cost of staying in control are too high due to manual work (IT controls are not automated and/or continuously monitored).
- Your IT Management processes are not set up effectively and (IT general) controls are not effectively designed and implemented IT.
- You want to lower the costs and increase effectiveness through optimisation and automation.
- You need to initiate a large transformation, IT or ERP program but do not know where to start and how to control and govern.
- You need to align your business and IT strategy and organise your IT partners, IT operations and Maintenance and /or need an independent view on IT partners and technology.
IT Governance and Compliance and IT (project) control
- You need to define setup and/or align your business and IT strategy and organise your IT Security, IT partners, IT operations and Maintenance and /or need an independent view on IT partners and technology
- You need to initiate a large transformation, IT or ERP program but do not know where to start , how to staff and control these projects and how to ensure to be (e.g. SOX) compliant after go-live
- Your cost of compliance is too high or you are facing high risk IT/ ERP security and compliance issues.
- Your IT and compliance governance is not set up effectively, leading to non-compliances and (ERP) audit findings
IT (ERP) security and Control
- Your IT reveals compliance issues and/ or audit findings, eg AD / SAP/Oracle security, IT-controls, Identity Access Management, or SoDs and authorisations.
- Do you have Security / SOD challenges or you do have insufficient insight in the security SOD risks your within your (ERP) systems?
- Do you want to lower your cost and increase the quality and automation of the of IT General Controls
- Are you depending on or individuals, lack of flexibility or do you have problems in staffing your team regarding the maintenance of your (ERP) security?
- Are you facing SAP license compliance fines?
- Is there a need to rationalise, automate or simplify your (IT) controls framework?
Technology, specialist consulting & managed services
Our propositions
Strategy, governance and structure
- Strategic IT consulting (workshops or coaching) to define What you want/need to realise to be effective (vision, added value, planning, maturity plateaus), resulting in a concrete IT or IT Security and Compliance program (How).
- Baseline assessment to determine identify risks, challenges and improvement opportunities
- Consulting to define effective governance organisation to stay compliant or keep your authorisations and security clean and SOD/ risk free
- Co-source or fully outsource your ERP / AD Security and compliance function.
- Setup governance organisation to ensure business and IT alignment, define business and IT roles & responsibilities and related user rights, manage strategic projects and ensure compliance after the change / IT project
Policies & processes
- Hands-on consulting to build your IT management and maintenance processes, policies and procedures
- Setup, update, optimise or automate design and implementation (IT general) controls and ensure effective security and SoD
People
- Training and or control awareness, on IT controls, soft controls, and integrity controls.
- High quality specialist on expert areas to improve your compliance within your IT environment by
- cleaning up (get clean) and getting compliant by (re) designing your SAP authorisations, redesign and implementation of Segregation of Duties (SoD)
- Implementation of improvement activities, setting up governance organisation and change management activities to stay clean and compliant.
- Ad-interim IT/ ERP and Security and compliance professionals
- Repetitive IDM / IT Security work as managed service. Provide flexible Dutch and English speaking compliance staff at your location, out of our service centres, or hybrid.
- SAP Security managed service
- Manage identified risks or mitigate financial or internal audit issues
- Change, program and project management capabilities and /or project and compliance related roles as test management, design and implementation of (IT) controls and security
Technology
- Help to select technology to improve compliance quality and lower costs often with content and frameworks included.
- Automate and continuous monitor your IT General Controls
- Automate and continuous monitoring of your (SAP) compliance (SoD, authorisations, security, data).
- Implement ERP GRC and security software; agile, in-time, and at a fixed price.
- Analyse, optimise and improve your SAP Licensing to prevent fines and to be compliant.
- Analyse your processes and SAP-landscape to determine risk, compliance and improvement area
Our solutions
IT controls & security technology
Unleash the power of our Security and Control Technology, designed to be in control and manage your security risks
Our comprehensive suite of technology and services empowers you to analyse, automate, and optimise your security, compliance, and risk management processes, ensuring efficiency, effectiveness and compliance.
Our services include:
- Implementation of SAP security and Compliance (GRC) technology
- Optimisation of Security and control (GRC) Technology Usage: Maximize the value of your technology investments with our optimisation services.
- Application Security: Protect your critical assets applications with our robust application security solutions.
- IT GRC Software Integration: Seamlessly integrate your IT GRC software with other vital systems, such as risk management and internal audit platforms.
- (Cyber) Security and control (GRC) technology Selection and Implementation
IT controls & security consulting
Our Security and compliance specialists help clients to assess compliance risks and control effectiveness, improve control effectiveness and minimise risks (get clean and compliant) and embed to stay compliant and clean.
Our services include:
- Baseline assessment to determine and identify risks, control weaknesses and improvement opportunities
- Strategy and roadmap development to achieve your risk and compliance and efficiency goals
- Improvement services (get clean and compliant ) activities to design, implement and efficiency opportunities and mitigate key risks
- Implementation activities to stay clean and compliant by implementing governance models, improvement activities and operating effectiveness of IT controls
- Design, implement, automate and continuous monitor your (IT General) controls
IT control (SAP) managed services
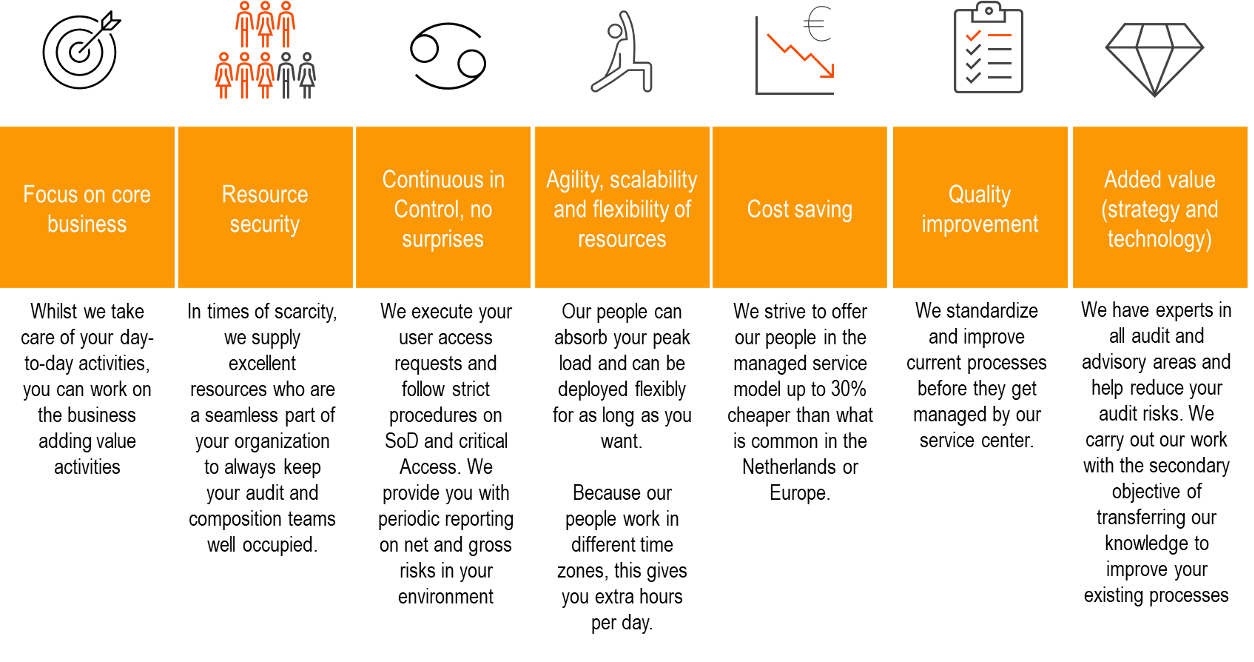
For clients who want to focus on their core businesses, not rely on individuals and want to get rid of their security, SoD and compliance risks (and audit findings) can outsource their security activities to BR1GHT.
We implement a stay-clean governance model and automate IT general control procedures as much as possible.
- Our team is scaled for speed, quality, agility, reduced risk and efficiency which leads through consistent professional support, you are not depending on single individuals
- We solve your low and medium complexity SAP security issues within agreed timeframes
- We can (temporary) scale up our team in case of high complexity issues or projects
- We define the support activities upfront for a fixed fee per month
Business & IT alignment
We offer a broad overview of CIO’s services where we can support you on:
- Lowering the cost of (IT general) controls by automation and continuous monitoring
- Challenging and giving an independent view on business and IT alignment
- Strategic discussions, and managing and controlling strategic change and transformation programs
- Setting up (agile) governance model, management information and partner management
- Supporting in the strategic decisions on Security, controls and controls integration
IT change control
For CIO’s and program / project managers we offer services to control and manage their critical change programs by:
- Continuous control (Walk along”) on ERP program, including benefit tracking, project management, quality assurance, and training.
- Stage gate assessments.
- Review and setup of the governance reporting within projects.
- Test management and automation.
- After live support and migration from project to maintenance mode.
- Deep dive activities to support on certain areas.
Client Experiences







Technology

SAP GRC solution
Soterion is a technology, delivered and implemented by BR1GHT that focuses on identity management and the compliance on SAP Security. It provides robust capabilities to manage user identities, control access permissions, and ensure compliance across various systems and applications within an organisation. Soterion aims to enhance security, streamline operations, and enable efficient management of user access.
BR1GHT offers key value drivers for Soterion:
- Business Accountability: Enhances SAP Risk and Compliance involvement.
- Enhanced Security: Strengthens security through robust measures.
- Improved Compliance: Assists in compliance management and audit trails.
- Operational Efficiency: Streamlines user access workflows and reduces overhead.
- User Experience: Provides seamless, self-service access management, improving satisfaction.
- Scalability and Flexibility: Accommodates evolving organisational needs efficiently.

Risk & compliance
Security Bridge is a easy to use technology who protects your SAP system. It is able to do real time intrusion detection, security configuration reviews, interface trafffic monitor, patch management reviews, code vulrenability management and transport center review for SAP.
Security Bridge is a crucial component of BR1GHT’s comprehensive security solutions. With Security Bridge, we can provide our clients with unparalleled visibility, control, and management of their security infrastructure. This powerful platform integrates various security tools and technologies, allowing us to offer real-time monitoring, threat detection, incident response, vulnerability management, and security analytics. By leveraging Security Bridge, we empower organizations to proactively protect their IT environments, mitigate risks, and ensure regulatory compliance. Together, we deliver robust security solutions that safeguard critical assets, enhance resilience, and enable our clients to confidently navigate the complex threat landscape Security Bridge is a easy to use technology who protects your SAP system. It is able to do real time intrusion detection, security configuration reviews, interface trafffic monitor, patch management reviews, code vulrenability management and transport center review for SAP.
Security Bridge is a crucial component of BR1GHT’s comprehensive security solutions. With Security Bridge, we can provide our clients with unparalleled visibility, control, and management of their security infrastructure. This powerful platform integrates various security tools and technologies, allowing us to offer real-time monitoring, threat detection, incident response, vulnerability management, and security analytics. By leveraging Security Bridge, we empower organizations to proactively protect their IT environments, mitigate risks, and ensure regulatory compliance. Together, we deliver robust security solutions that safeguard critical assets, enhance resilience, and enable our clients to confidently navigate the complex threat landscape

Transaction monitoring
Pathlock is able to perform automated SoD reviews, user access reviews, provisioning, firefighitng management, vulrenability management, code scanning and thread detection and response in a SAP. Next to that Pathlock is able to perfom cross system SoD analysis and risk quantification
Pathlock is a valued partner that adds significant value to BR1GHT. Their expertise in governance, risk, and compliance (GRC) solutions complements our offerings, allowing us to provide comprehensive security and compliance solutions to our clients. With Pathlock’s advanced GRC platform and their deep understanding of regulatory requirements, we can deliver robust access control, risk management, and compliance automation capabilities. Together, we enable organizations to proactively manage risks, strengthen security, and ensure compliance with industry regulations. By combining our expertise, we empower our clients with the tools and insights needed to safeguard their critical assets and achieve their business objectives.

Audit & controls
EPI USE Labs is a strategic partner that brings immense value to BR1GHT. Their expertise in SAP and data management solutions complements our capabilities, enabling us to deliver comprehensive, end-to-end solutions to our clients. With EPI USE Labs’ deep understanding of SAP technologies and their innovative approach to data management, we can leverage their cutting-edge tools and methodologies to enhance our services, optimize SAP landscapes, ensure data quality, and drive business transformation. Together, we are well-equipped to empower organizations with robust solutions that maximize the value of their SAP investments and accelerate their digital journey.

GRC solution
Leapwork is a valuable partner that brings significant value to BR1GHT. Their powerful test automation platform enhances our capabilities, enabling us to deliver exceptional quality assurance and testing solutions to our clients. With Leapwork’s intuitive, codeless automation tools and extensive library of pre-built automation components, we can accelerate testing cycles, improve efficiency, and ensure reliable software delivery. Together, we empower organizations to achieve faster time to market, enhance product quality, and streamline their testing processes. By leveraging Leapwork’s cutting-edge technology, we offer comprehensive automation solutions that optimize business operations and drive digital transformation for our clients.
reach new heights with our world class technology software
meet all compliance regulations
continuous dialogue with all your stakeholders inside and outside your organisation
company wide dashboards providing real-time insight
Full transparency towards all stakeholders
IT Security and Control proposition

Why IT / SAP security & compliance?
A company’s application landscape is often complex by design and is becoming more and more complex IT environments, with multiple SAP environments and or SAP solutions (ECC, S4HANA, Concur, SuccessFactors, Ariba, Fieldglass), all working together with other non-SAP best-of-breed solutions. On premise, in the cloud or as combination of both. The context is often not stable, with increasing demands and an ever-increasing pace of change. Our SAP security & compliance proposition covers every angle of your SAP risks in both a ‘SAP-only’ environment and a diverse complex application environment.

Our value propositions
We always start with best of breed technology to capture, enhance, and protect your business value. However, our proposition always includes a result-driven implementation approach, pre-defined content, and capabilities to make the changes stick by transferring our knowledge to your people.
Please find below a detailed description of our SAP security & compliance value propositions.
Control
Our SAP control solutions help you in your journey to zero trust[1].
SAP Cyber Security is becoming increasingly important. Although 70% of security breaches occur internally, external cyber threats to your SAP-environment together with custom code risks cause many problems. Our SAP security technologies platform provides the best threat detection, vulnerability management, code analysis, interface traffic monitoring, patch management, and incident response on the market today.
Integrated SAP GRC. We can support our clients with the customisation of the GRC solution of SAP themselves, but we also offer cost effective alternatives, both for access (authorisations) and process controls. Our technology can interface with almost any Compliance, Risk or Audit Management System, providing you the capabilities to automatically link your SAP controls to your risk universe, compliance areas or audit plan. Controls are only defined once and the effectiveness of your SAP controls can be presented at any time, against any risk or compliance area, and in end-user understandable language. To save time and guarantee quality, we work with pre-defined rulesets, derived from your financial auditor’s’ best practices.
Data compliance & GDPR regulations are areas many companies struggle with. Our solutions provide you with the capability to manage your SAP data compliance, in any environment (test, acceptance and production), securing encryption in transit and intelligent scrambling & masking technologies for testing.
SAP security & compliance capabilities are scarce. During our involvement we train your SAP experts and their roles & responsibilities. We do this in your user and IT-departments (Centre of Excellence), whether you work via projects or in agile dev/ops teams. In all cases we over our SAP security & compliance capabilities as a ‘managed service” out of our global network. This can be an ideal solution for many reasons, such as cost saving, non-core outsourcing policy or inadequate access to specialist resources.
In summary, our propositions apply to the following use case and client experiences:
- SAP Cyber Security.
- SAP custom code review.
- SAP GRC auditing, design, and testing.
- Interfacing SAP with GRC or Audit Systems.
- SAP data privacy over testing, production, and transfer.
- SAP security & controls knowledge transfer.
- SAP security & compliance ‘as a service’
- Thread and interface vulnerability management;
- SAP Augmented Access Control (AAC).
[1] Zero Trust is a shift of network defenses toward a more comprehensive IT security model that allows organizations to restrict access controls to networks, applications, and environment without sacrificing performance and user experience. In short, a Zero Trust approach trusts no one. As more organizations do more computing outside their perimeter in the cloud, security teams find it increasingly difficult to trust or identify who and what should be allowed or trusted with access to their networks. As a result, an increasing number of organizations are adopting Zero Trust as an element or a component of their trust network architecture and enterprise security strategy.
Operate
Our IT Security and Control service centre in South Africa operate solutions help you to monitor your processes continuously with a special focus on controls.
SAP and IDM security and control
- We perform 1rst, 2nd and 3rd line of AD and SAP security incidents and projects
- We can be your liaison between your external auditor and perform (pre) audit support
- We can do the operational security and compliance management
- Execute your IT general controls
- We ensure your stay compliant and limit your IT audit findings
Continuous Controls Monitoring
- We monitor 100% of your transactions, real-time, with the capability to remediate immediately (preventive controls).
- We are able perform a continuous delivery of controls design, testing, implementation and maintenance for a fixed price.
Improve
Our SAP Improve solutions help you to identify process complexities and provide you a roadmap for simplification.
Our data & process mining solutions analyse your processes for discovering, monitoring, and improving processes as they are (not as you think they might be). This offers objective, fact-based insights, derived from actual data that help you audit, analyse, and improve your existing business processes by answering both compliance and performance related questions. Together with the mentioned role-design analytics, our solutions provide the needed information to identify and remove complexity, better utilise your SAP-system, and improve control. Our methodology identifies a) unnecessary complexity (unused functionalities or ‘deadwood’, unnecessary customisations, better unified and simpler solutions), and b) accepted complexity (because your processes are complex).
When starting your improvement journey, always start with the end in mind. For SAP clients this is the conversion to S4 HANA cloud. Our software directs and guides your improvements to make your transition programme a conversion and not a new implementation, saving you time and costs.
In summary, our propositions apply to the following use case and client experiences:
- Data & process mining
- SAP Data Management.
- Role-design complexity analysis.
- Full support to reduce complexity
Challenges at our clients
- Lack of an understanding of the design and operating effectiveness of your SAP authorizations & controls and your SAP security.
- Insufficient insight in the cross-SoD risks and controls effectiveness within a (hybrid cloud) ERP landscape
- IT general controls as user access requests, firefighting, user / role certification are manually executed and high risk
- High amount of SoD conflicts and key audit findings
- Business is not aware of SAP security risks
- SAP security is focused on SAP application security and to a lesser extend to database, operating system, network and cyber security
- Limited integration within SOC (network security) and non secure communication protocols
- Insufficient insight in risks on custom made developments (reports, interfaces and transaction codes)
- Business not aware of the risks as (SoD) risk analysis is not automatically executed upon user access / change request
- Organizations have challenges to “stay clean”
Ineffective governance and resourcing challenges on SAP Security and Compliance
What we do we offer
- We offer you a highly skilled team. Our specialists are certified and maintain their competences by continuous learning. You have one single point of contact for the daily operations. We Seamlessly work with your people, under your management supervision and in your risk, quality IT management systems.
- Experienced Dutch and English-speaking specialists knowing your culture and local requirements.
- We implement a stay clean governance model and automate IT general control procedures as much as possible
- We solve your low and medium complexity SAP security issues within agreed timeframes
- We can (temporary) scale up your team in case of high complexity issues or projects
- Long term dedicated strategic partnership investing in quality.
- Long-term staff availability with maximum flexibility.
- Focus to improve your compliance and your processes.
- Fixed price, flexible scaling, up to 30% cost saving.
- We offer you our global capabilities and footprint with local market expertise with the right combination of industry, technology, process, and full lifecycle assets
- Availability between 9 am till 17 pm Surinam time. On call support for Priority 1 Issues.
Value of BR1GHT’s Managed service model
BR1GHT Managed Service Growth Model

SAP Managed services capabilities

